Table Of Contents

Today I’ll let you into the domains of my demo environment. Together we will enable Microsoft Defender for Endpoint, connect it with Microsoft Intune, and onboard devices.
Defender for Endpoint is an enterprise endpoint security platform created to help businesses manage threats. It directly integrates with other Microsoft Solutions, such as Microsoft Purview. Defender for Endpoint is a prerequisite for Endpoint Data Loss Prevention (DLP) and Insider Risk management.
We will also touch on how signals from Defender for Endpoint can be used in Intune Application Protection policies and device compliance.
First, let’s look at what we need…
Prerequisites
- We need Microsoft Intune licenses and Defender for Endpoint P2 licenses
- We need Intune Administrator and Security Administrator roles to configure the portals.
- We need one or more devices enrolled and managed by Intune. My coworker and friend Ola Ström ☁️💻 has written an educative guide Intune lab for noobs and Part 3- Windows is what you are looking for if you want to learn the basics.
You can also read here about the Prerequisites
Enable Microsoft Defender for Endpoint
Sign in to Intune (https://endpoint.microsoft.com)
Select Endpoint security, then Microsoft Defender for Endpoint, and then select Open the Microsoft Defender Security Center.
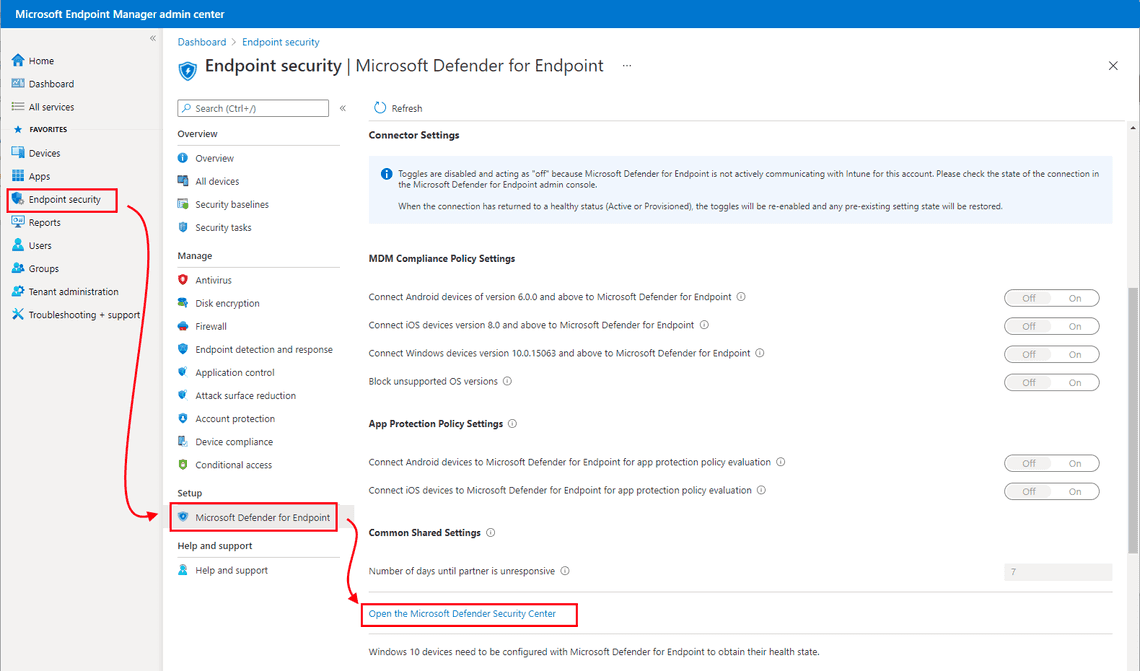
Before connecting the services, the link says, Open the Microsoft Defender Security Center. After you have turned on the connection to Intune, the UI changes, and the link says, Open the Microsoft Defender for Endpoint admin console.
Inside the newly opened Microsoft 365 Defender portal, scroll down in the left navigation and select Settings
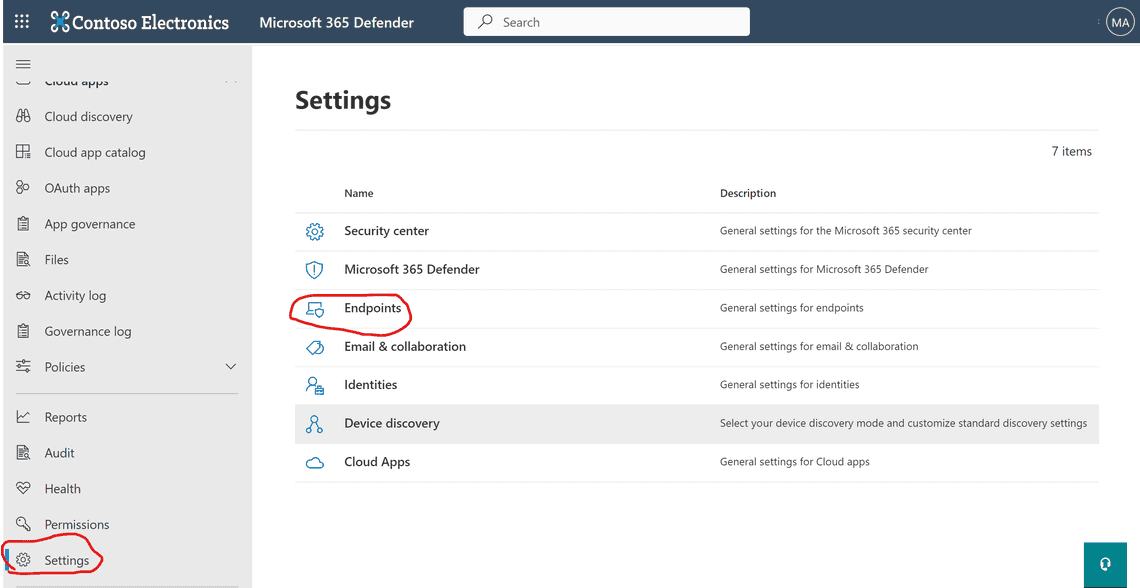
Select Endpoints and then Advanced features
Scroll down to the Microsoft Intune connection, turn the toggle to On and Save Preferences.

At this point, Microsoft Defender integrates into Intune. You can check the status in the Endpoint security menu.
Please return to the Microsoft Defender for Endpoint page in Intune, where we will configure some Policy settings.
MDM Compliance Policy Settings
We want to enable Defender for Endpoint with Compliance Policies. So we will turn on iOS and Windows devices under Compliance policy evaluation. Now our current managed devices, and devices you enroll in the future, are connected to Microsoft Defender for Endpoint for compliance.
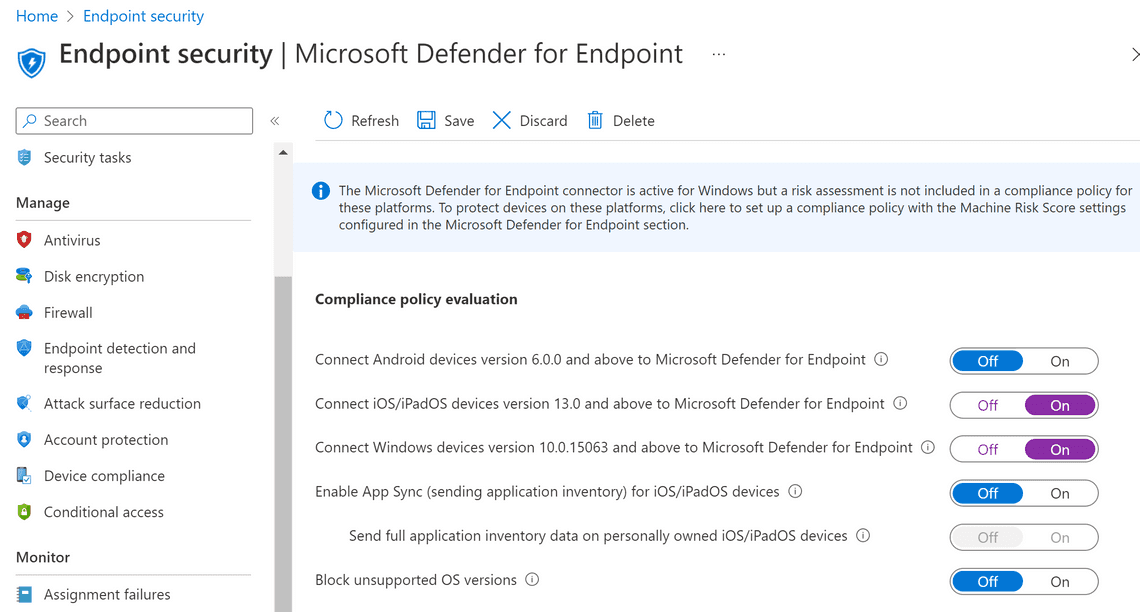
Device Compliance
In my post Device Compliance Overview, you can read more about Compliance policies in Intune.
Threat level classifications are determined by Microsoft Defender for Endpoint. For example, we can now create a policy that requires the device to be at or under the machine risk score to your preferred level. In Zero Trust identity and device access policies Microsoft recommends medium.
You can read more here on how to Create a Device risk level Compliance policy
App Protection Policy Settings
We also want to use Defender for Endpoint with app protection policies, so we will turn on iOS devices under App protection policy evaluation.
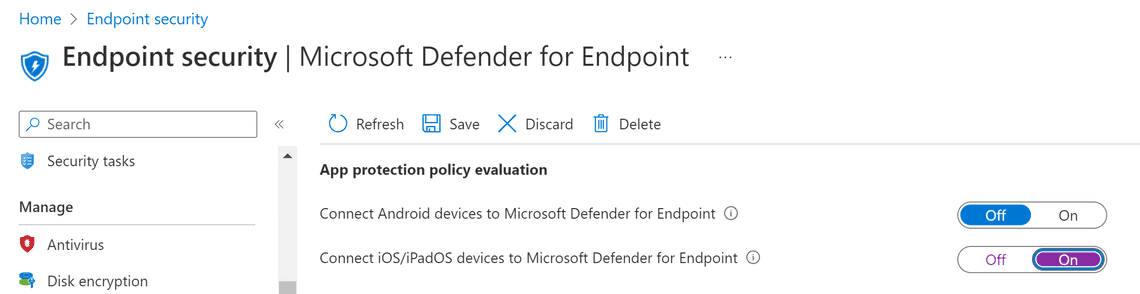
App protection policies
Ola Ström ☁️💻 wrote a guest blog post around App Protection Policies.
We can use the risk signals from Defender for Endpoint to determine if we want to selectively wipe or block any app.
You can read more here on how to Create a Mobile Threat Defense (MTD) app protection policy with Intune
Onboard Windows devices
After you connect Intune and Microsoft Defender for Endpoint, Intune receives an onboarding configuration package. You can use a Device configuration profile or an Endpoint detection and response (EDR) policy to deploy the package to your Windows devices. Make sure to select only one to prevent policy conflicts for devices.
I’m using the EDR policy, which is more lightweight than device configuration profiles. So, for example, we can use the onboarding package from Defender for Endpoint, so we don’t need to manually configure a package.
Sign in to Intune (https://endpoint.microsoft.com) again
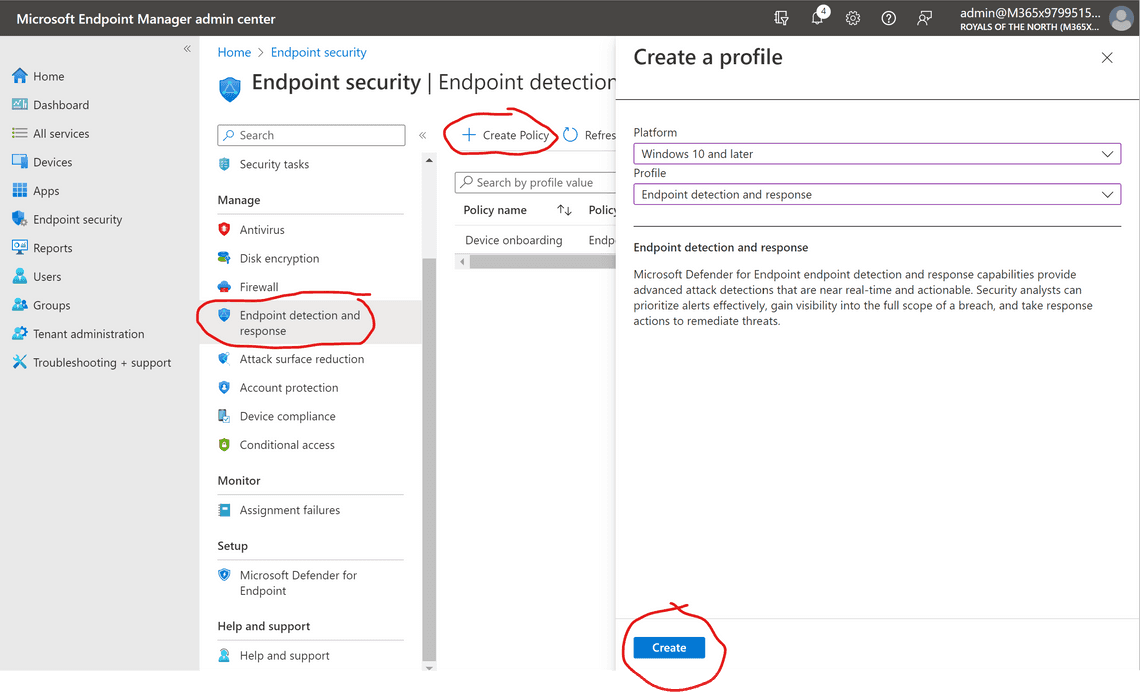
Go to Endpoint security followed by Endpoint detection and response
Select Create policy, select Windows 10 and Later and Endpoint detection and response and finally Create
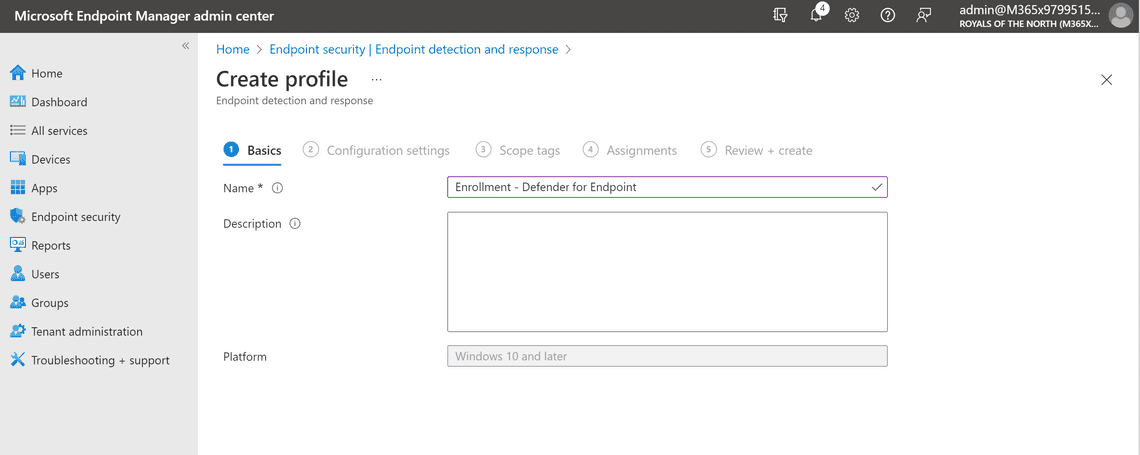
Enter a Name and Description, click Next
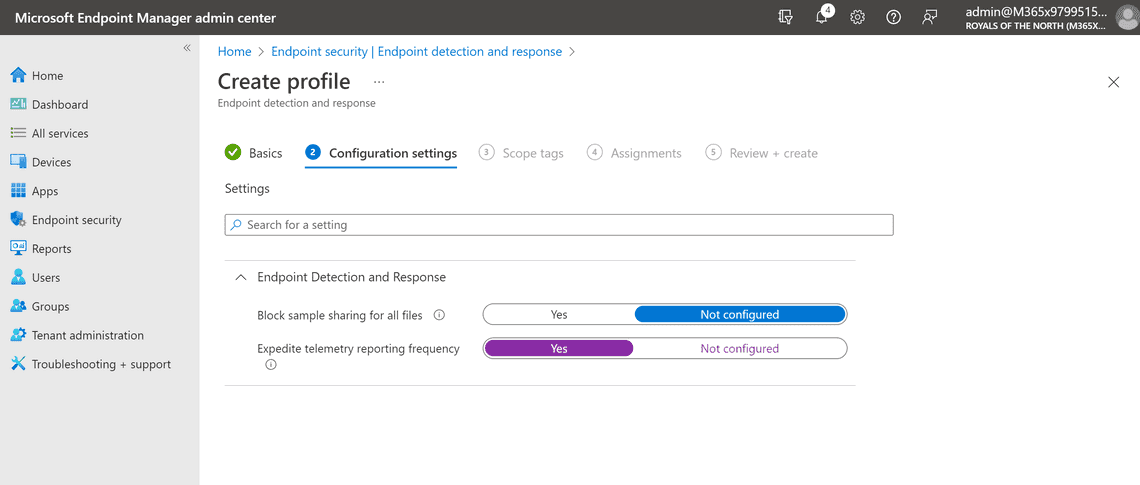
Enable the Expedite telemetry reporting frequency setting and click Next two times.
I selected Add all devices here.
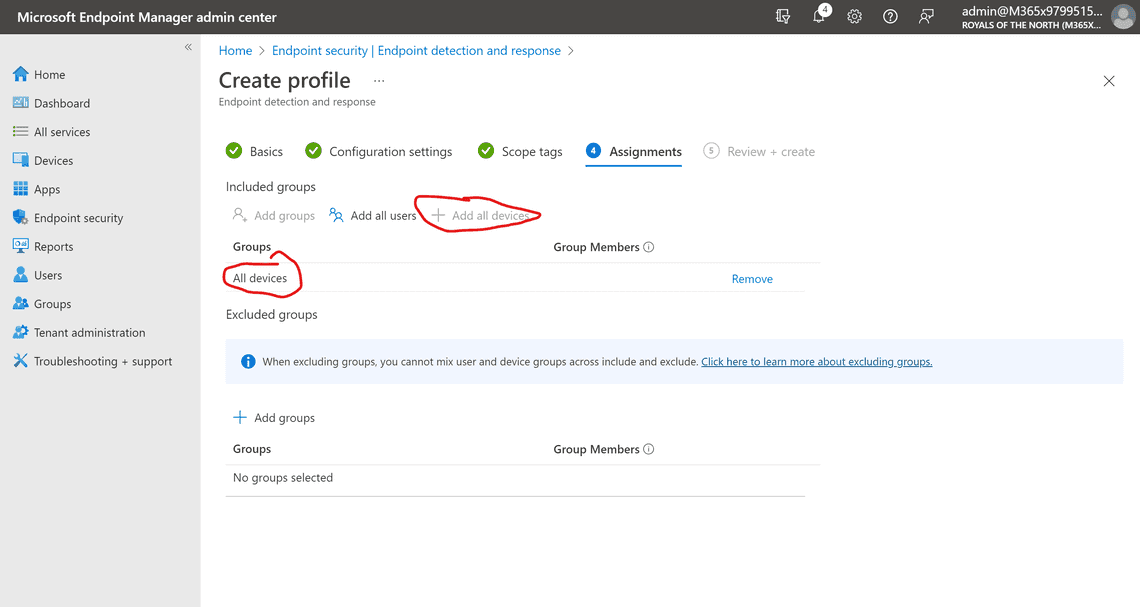
Click Next and then Create to create the profile.
Confirm that the rule is saying Yes, under assigned. If you check the devices, it might say pending for a few hours until it has been applied.
Summary and next steps
This small blog post grew into something more extensive than I had planned for. We did only scratch the surface when it comes to Defender for Endpoint. But now we have it working; we have enrolled devices and the possibility to create extraordinary policies for mobile and desktop, and even use Microsoft Purview features.
Thank you for reading
/Simon
Related Posts