Today, we are using our mobile devices a lot, this could be either phones or tablets. Within the corporate world, mobile device management is often used to secure the devices. Mobile device management, MDM, is great, but that has a strong focus on securing the device. What about securing the data, and securing data on unmanaged devices?
Within the Microsoft Intune product suite, there is something called Application Protection Policies, or APP for short. This is a security layer which can be added to supported applications, even if the device is not managed. This is usually referred to as Mobile Application Management, or MAM.
Since Microsoft is calling this feature APP, that is the term we will keep to.
What you can do with APP?
APP can be used to put policies on apps where you store corporate data, and you can also use APP as a condition in Conditional Access, that a managed app needs to be used to access the data. This means that no matter what mobile device you add your corporate account to, the settings will apply even if the device is not managed. When the account is removed, settings are removed. The settings we apply ONLY applies for the corporate bubble in the application, so if you have a personal account in OneDrive, that wont be affected.
This means that we can set policies on an application level which controls what the users is allowed to do, and not do. We can also put conditions on the application which needs to be fulfilled before gaining access, not really like Conditional Access but we do have a few switches such as making sure that the device is not rooted/jailbroken and that we are running above a certain version of the OS.
A typical thing you would do with APP is to limit the possibility of copy/paste to applications which are not managed, to minimize the risk of that things are being copied in a uncontrolled way. You would also typically control how and where corporate data can be saved, only allowing SharePoint and OneDrive for Business for instance.
The basics
Application Protection Policies (APP) is only available in Intune, but you do not need to manage your devices with Intune, but you will need licenses to use Intune for your user (e.g. M365 E3/E5 licenses or EMS E3/E5 licenses).
You also need an Azure AD, since we are dependent on your identity to get the settings out to the devices.
To configure APP, we will head into the Intune portal (endpoint.microsoft.com), which means that you also need a admin user in Intune. Typically the Azure AD role Intune Administrator is what you would use as an administrator, but Global Administrator or such will work to.
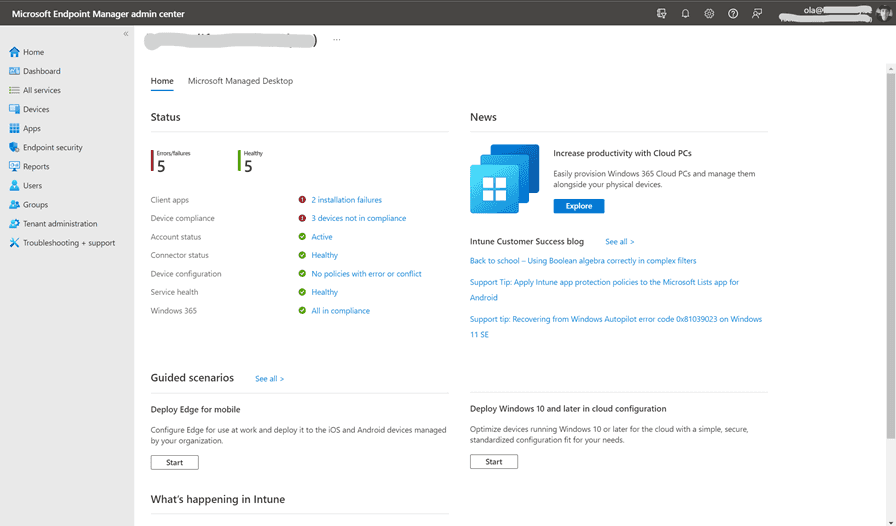
We will find the APP settings if we head to Applications > App Protection Policies
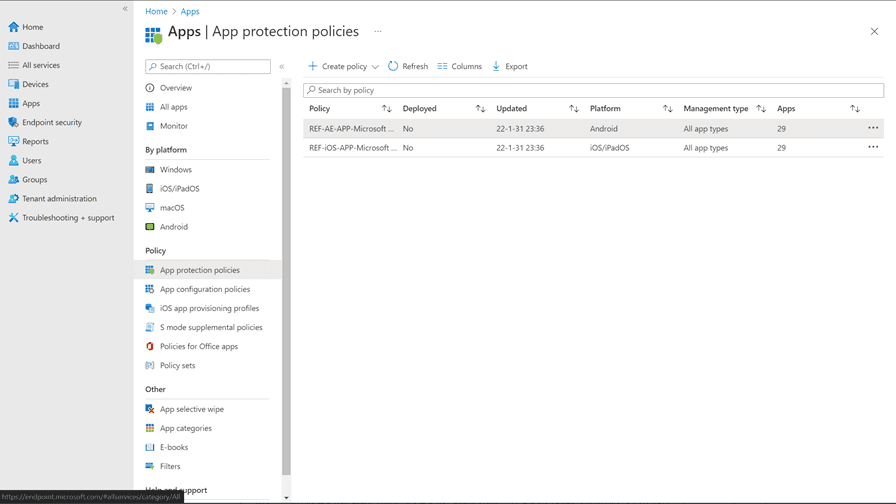
Creating a policy
To create our APP policy, click “+ Create policy” and select what platform you want to configure (iOS/iPadOS or Android).
Give your new policy a name and press next
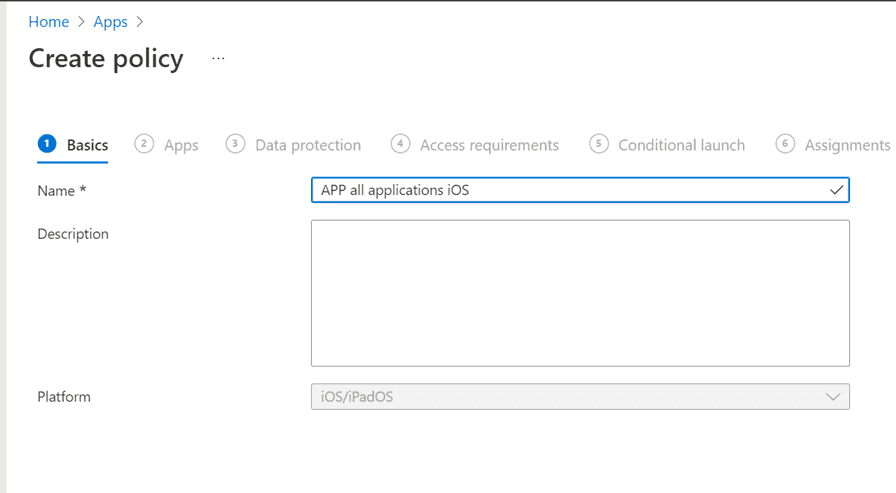
On the next page you will select what apps will be targeted and if you want to apply these to all devices, managed or unmanaged devices. In this example we will apply the policy to all devices, so we will leave the “Target to apps on all devices” to the default Yes. If you select no here, you will need to create additional app configurations for each application you are distributing from Intune to your managed devices. On “Target policy to” we can select what applications we what to target this to. In this example, we will target all apps, since we want to make sure that we secure all our apps. Then press Next.
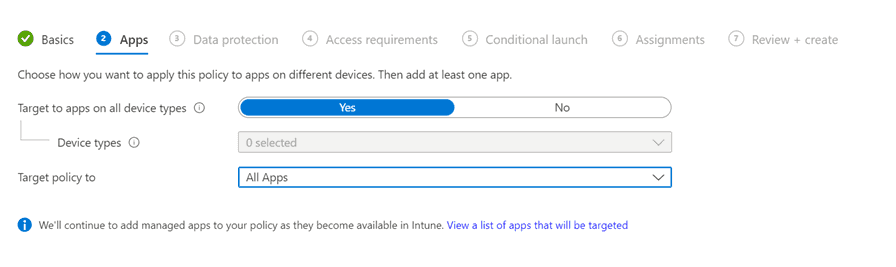
On the Data Protection tab, we will configure which settings we want to use to protect our data. These settings are different depending on which platform you configure this for. In this example I’m configuring for iOS, but there are similar settings for Android. There are a lot of settings you can do, and we will make some deviations from the default configuration. If we start with the Data Transfer settings, we want to ensure that users cannot backup any corporate data to their iCloud or iTunes backups.

We also want to limit the possibility to send organizational data to other applications than applications we manage. You can add applications, links and managed links which should be exempt, we will leave these to defaults.
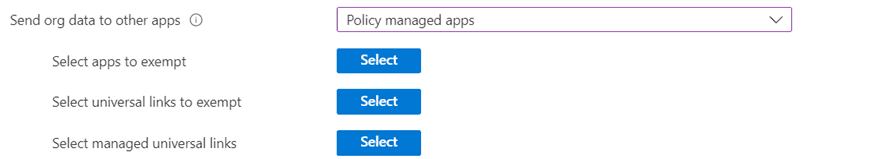
We will only allow that you can save organizational data to two defined sources, SharePoint and OneDrive for Business since these are the two cloud services we will use in this example.
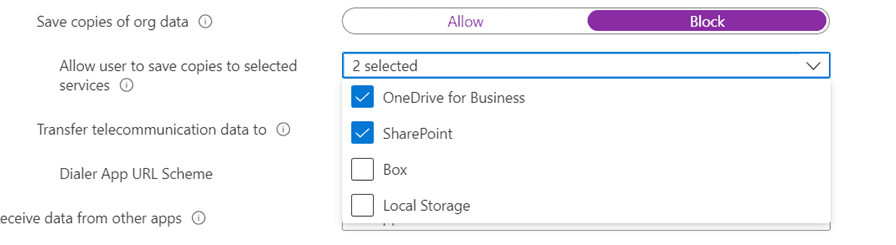
We will also make sure that we restrict cut, copy, and paste between other apps, we will only allow this to happen between policy managed apps.
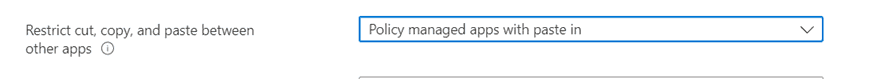
Under the Encryption and Functionality we will configure links to open in our managed browser, Microsoft Edge. All other values will be left to default values. Press Next to continue to the next tab.
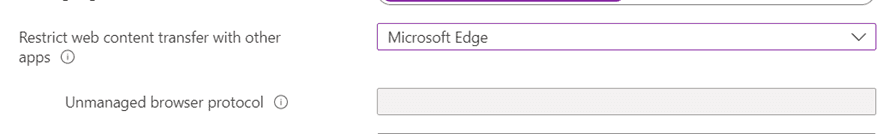
The next tab is Access requirements which controls how the application can be accessed. We will leave most values to their defaults, but we will change the PIN length to 6 digits. We will also change the “App PIN when device PIN is set” to Not required. This change will make the user experience a bit better when the device is managed by Intune since we can then ensure that PIN is present. For an unmanaged device we do not know if there is a PIN present or not, therefor we will require a PIN. When you have set the desired configuration, press Next.
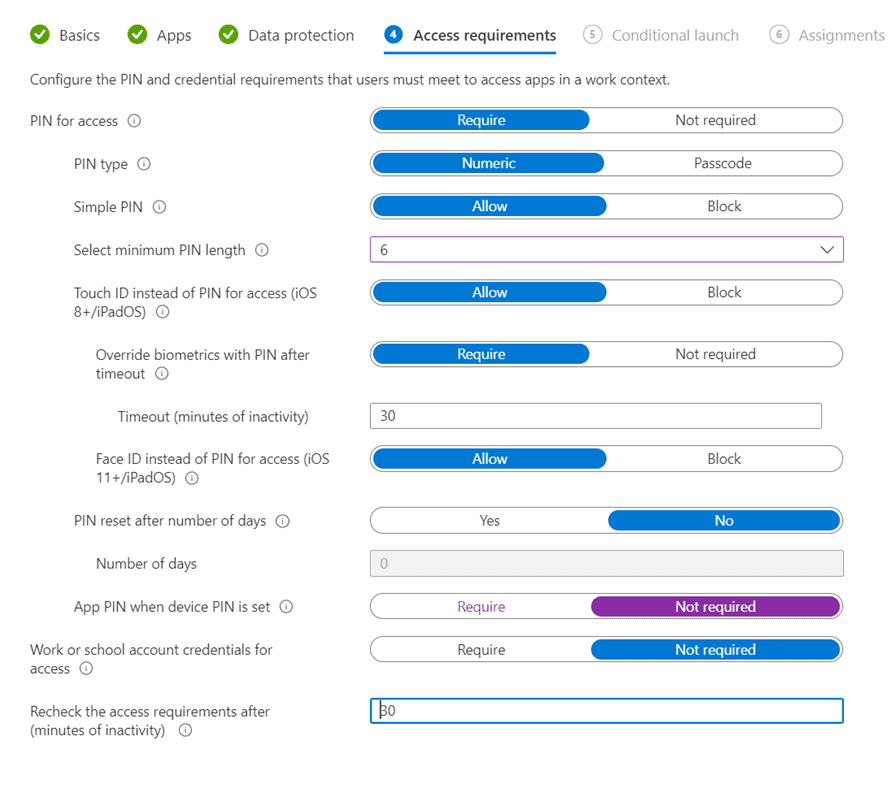
On the next tab we will set some conditions for how the application can be accessed on the device. We will leave all these to default values for this example and press Next.
In this tab, we can set add additional conditions if needed such as what happens if an account is disabled or if we require a certain level of OS version for the app to work.
On the next tab we will select what group we will target this to. Since this is a user settings, we will target a group with users. If there are a subset of users which should be excluded, we can add a group for that as well.
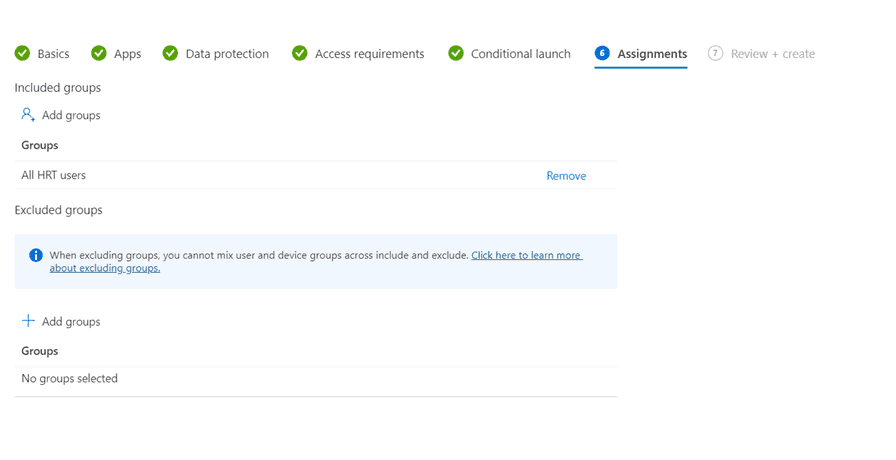
When you have added your user group, you will have the possibility to review your settings before you create the policy. When you have reviewed your settings, press Create.
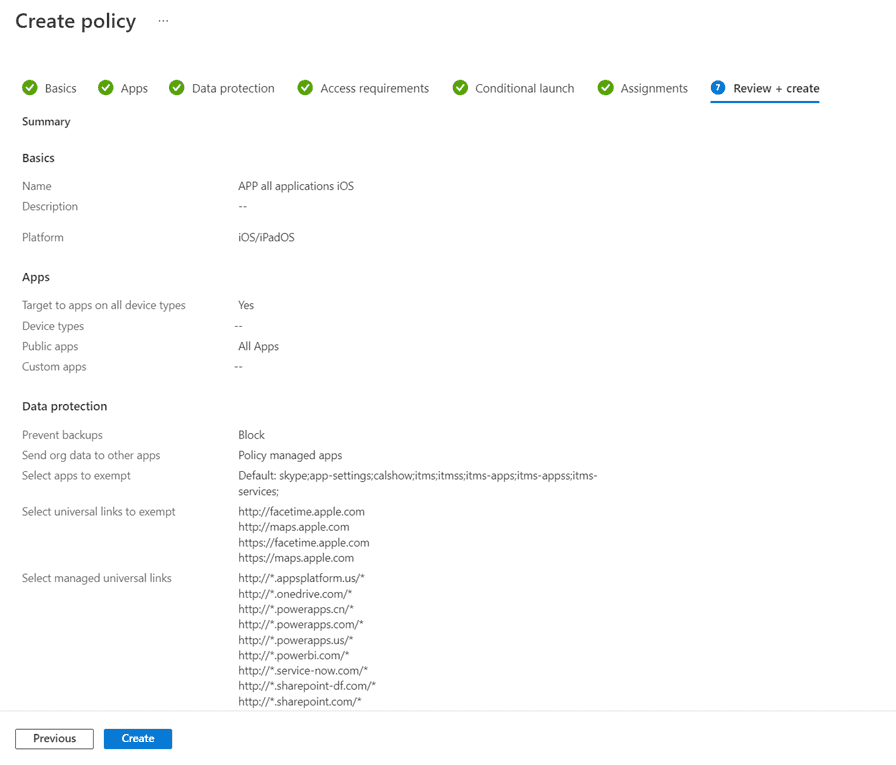
Summary and next steps
You have now learned what a APP policy is, why we should use them and how to create them. Simon will later show you how to use this policy with an Conditional Access Policy, and how the user experience is.
Related Posts