Introduction
Mobile devices have revolutionized our work, allowing us to access corporate data anywhere and anytime. However, this convenience also presents security risks, as employees may use unapproved apps to access corporate data, putting sensitive information at risk. Application protection policies (APP) can help mitigate these risks by enforcing policies on mobile apps. However, how can you ensure that only approved apps are used to access corporate data?
The answer is Conditional Access
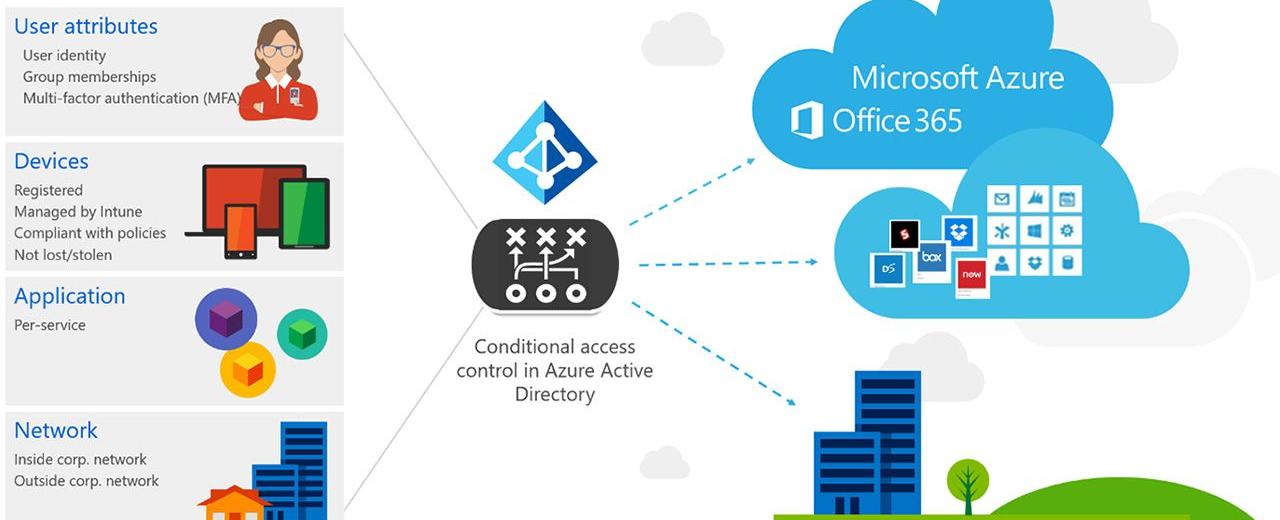
With Conditional Access Policies, we can control access to corporate data and resources based on specific conditions and restrict access to approved apps with APP. By combining Conditional Access with APP, organizations can ensure that only approved apps are used to access corporate data, reducing the risk of data leakage and unauthorized access. The best part is that this works with both organizationally managed and unmanaged (private) devices.
According to Microsofts Zero Trust identity and device access configuration Require approved apps and App Protection Policies should be incorporated in every tier, starting with baseline protection.
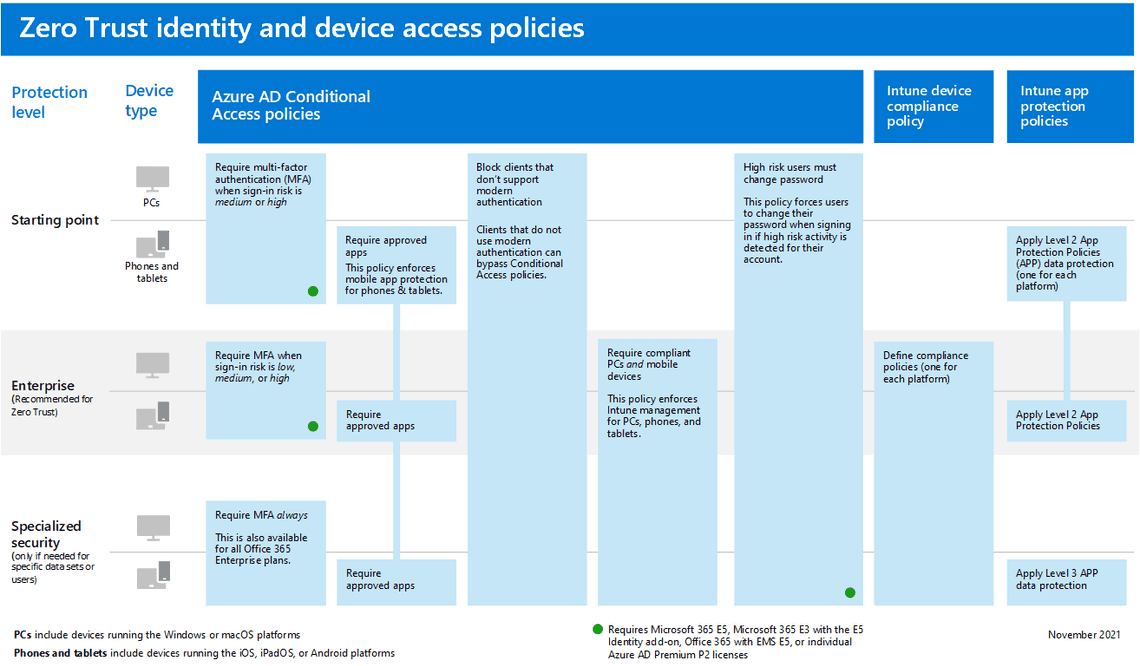
Why do we need Conditional Access if we already have APP and approved apps?
Let’s say our ambition is that no one should be able to copy company data from emails and paste it into any personal context, and we configure APP to work in this manner. Of course, the users could still use the native mail application in IOS and Android to sync the email, and APP would have no effect - the user could do whatever they want with the data.
It makes sense to block Exchange ActiveSync on all devices and disallow the usage of basic authentication from connecting to Exchange Online. And instead, have them use the Outlook app where APP is effective.
Creating a new policy
The easiest way is to create a new policy from a template. In Azure Active Directory -> Security -> Conditinal Access, you find New policy from template (Preview). Under the Zero Trust tab you find Require approved client apps and app protection.
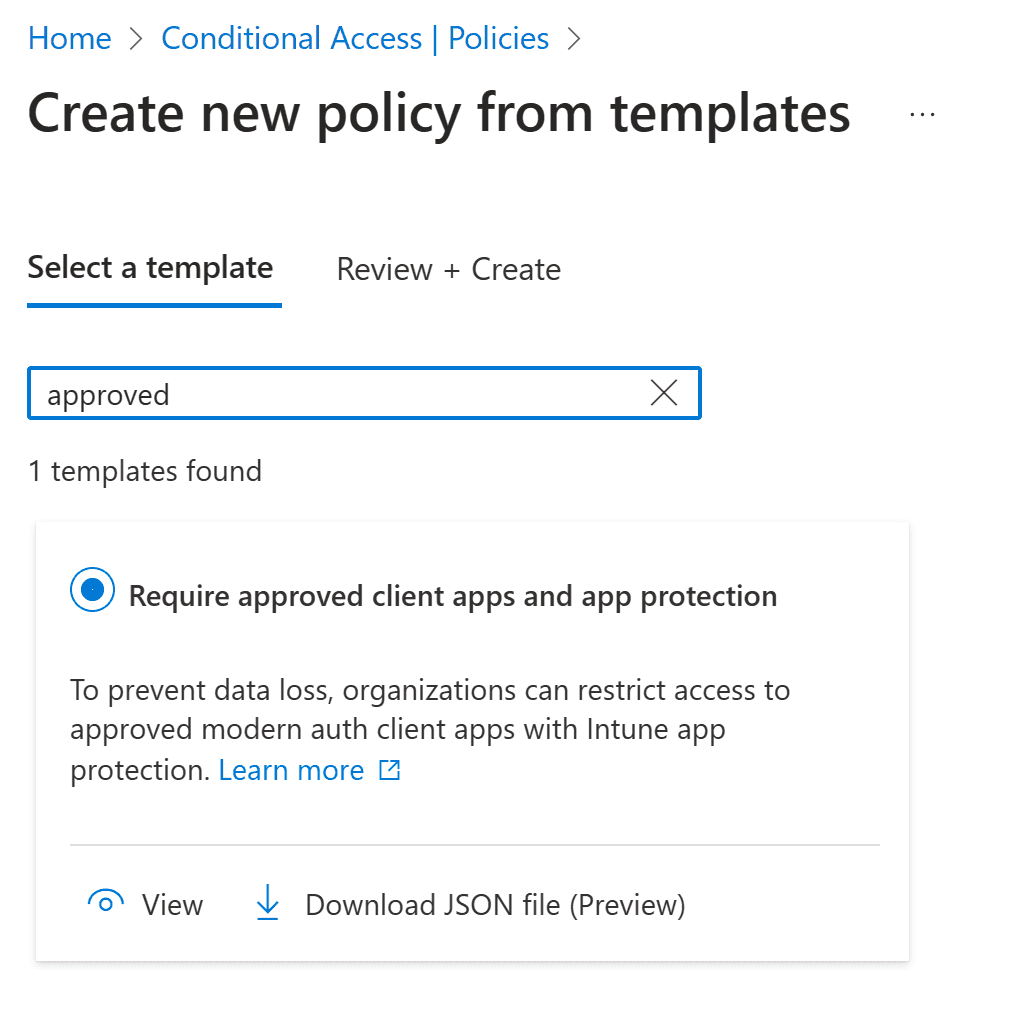
This one is configured for All cloud apps, for Iphone and Android, and to Grant but require both Require approved client app and Require app protection policy.
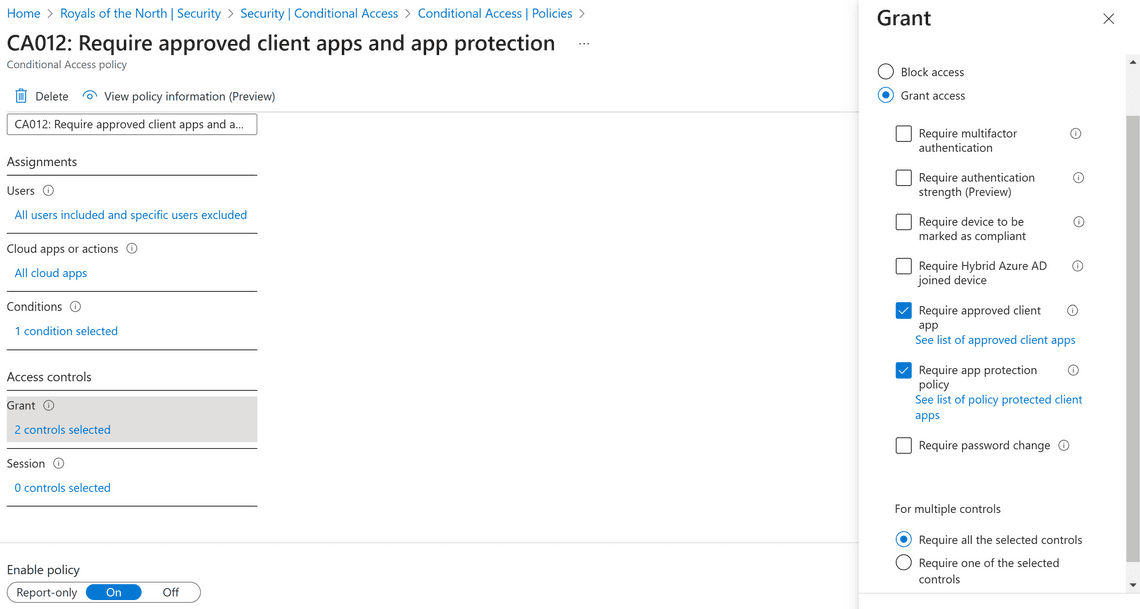
Assign the created conditional access policy to relevant users to restrict access to approved apps for corporate data security. This reduces data leakage risk, even in BYOD scenarios.
Thank you for reading
/Simon