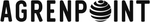Table Of Contents

A typical scenario is collaborating with people outside your organization. When you invite these individuals to a Microsoft Teams team, they become guests in our tenant and can access specific team resources.
The upsides
- Allowing guest access reduces shadow IT in the organization by enabling the end-user to collaborate efficiently with people outside the organization. Blocking will subsequently mean that your users will find another way to collaborate. Our best chance to apply good governance is if they stay inside the landscape.
- Let’s be honest: collaboration via email is not very fun or efficient compared to collaborating around files and conversations in Microsoft Teams.
We need to set this up at multiple places
Guest sharing is turned on by default for Microsoft 365 groups and SharePoint. However, sharing in Microsoft 365 is governed at its highest level by the B2B external collaboration settings in Azure Active Directory. If guest sharing is disabled or restricted in Azure AD, you can forget about all the other settings for sharing.
Azure AD External collaboration settings
In Azure Active Directory, under External identities and External collaboration settings, make sure that sharing with guests is not blocked and that the domains of the guests you want to collaborate with aren’t blocked. You may also want to restrict guests’ access to directory data under Guest user access restrictions.
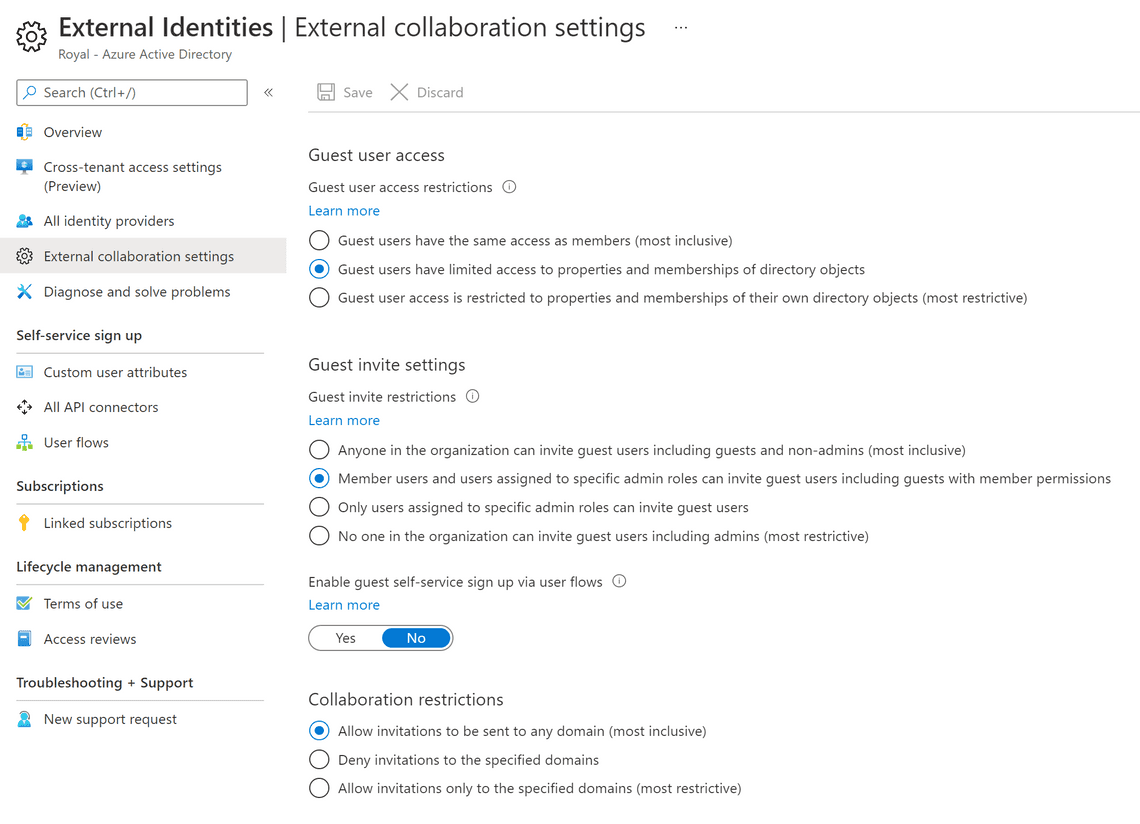
Microsoft 365 Groups guest settings
You must turn on the guest settings for Microsoft 365 Groups for guest access in Teams to work. In the Microsoft 365 admin center, under Settings and Org settings, click on Microsoft 365 Groups, ensure that no one has tampered with the default settings, and check both boxes.
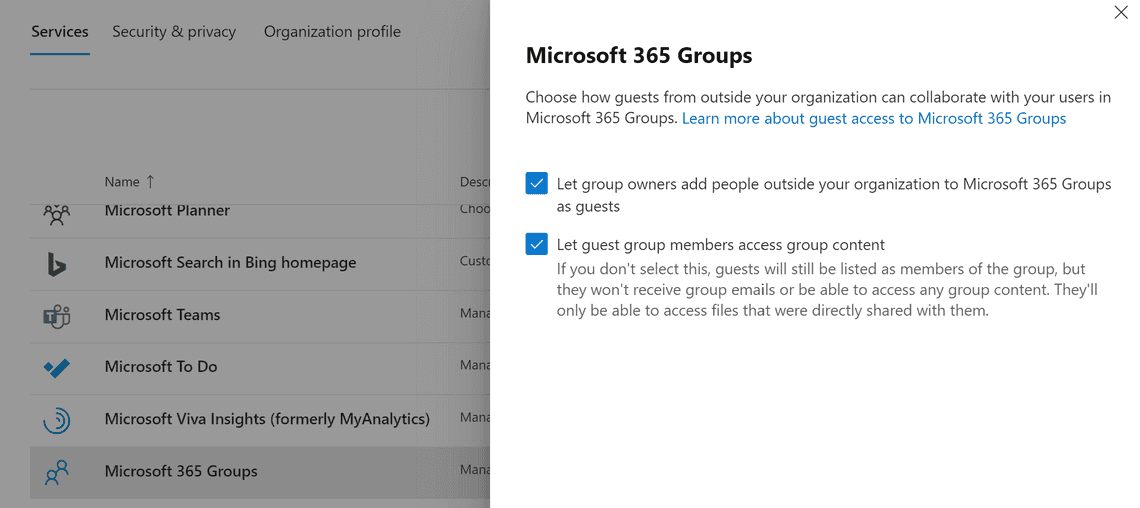
Teams guest access
You should enable guest access. In Teams Admin center, under Users and Guest Access, you find the master switch. Allow guest access in Teams must be On for guest access to work in Teams. You have the option to control guest access in individual teams and their associated SharePoint sites using sensitivity labels. Depending on your organization, you might want to disable guest access in confidential teams.
Challenges with guests
- Access to active teams: It’s hard to keep track of who should still have access to a specific team, no matter if it’s a guest or a user from the organization.
- Guests still in Azure AD: Many people think that the guests are automatically removed from the tenant by deleting a team. That’s not the case; the guest is still in the Azure AD and could at the very least still chat with other members of the organization.
- Risk of data loss: In general, not everyone in the organization knows what they are allowed to share with who, and it’s easy to overshare accidentally. And with guests in the team, the sensitive data might even leave the organization without proper governance in place.
Some good practices to finish with
- Enable Guest access in Microsoft Teams at the organizational level; limit specific teams by using sensitivity labels when required.
- Use sensitivity labels at the content level to protect sensitive data and Data Loss Prevention (DLP) to prevent accidental oversharing. More on this another time.
- Apply social control and educate team owners to manage guests in teams.
- If you have Azure AD P2 licenses, make sure to look at the Identity Governance features that make guest management easier:
We still need to look at sharing settings. So let’s do that in the next post.
Thanks for reading
/Simon